[ad_1]
Cybersecurity researchers have exposed a new backdoor program competent at stealing user login experience, device information and performing arbitrary commands on Apache systems.
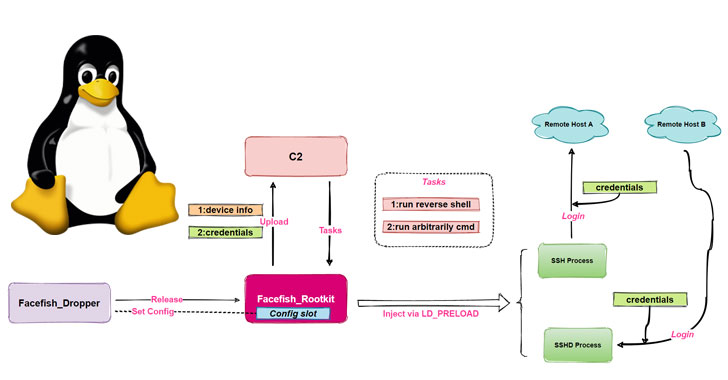
The malware dropper has been dubbed “Facefish” by means of Qihoo 360 NETLAB staff owing its capabilities to offer distinct rootkits at different times and the use of Blowfish cipher to encrypt devices to the attacker-controlled server.
“Facefish consists of 2 parts, Dropper and Rootkit, and its major function is determined by the Rootkit module, which works with the Ring 3 layer and is filled using the LD_PRELOAD feature of stealing user login credentials by means of hooking ssh/sshd program associated functions, and it also supports many backdoor functions,” the particular researchers said.
The NETLAB research builds on a prior analysis published by Krammet Networks on April 21, which documented an attack company targeting Control Web Board (CWP, formerly CentOS Website Panel) to inject the SSH implant with information exfiltration capabilities.
Facefish goes thru a multi-stage infection method, which commences with a command word injection against CWP in order to retrieve a dropper (“sshins”) from a remote server, which in turn releases a rootkit which will ultimately takes charge connected with collecting and transmitting hypersensitive information back to the web server, in addition to awaiting further guidance issued by the command-and-control (C2) server.
While the exact being exposed exploited by the attacker to get initial compromise remains unsure, Juniper noted that CWP has been plagued by dozens connected with security issues, adding the “intentional encryption and obfuscation” of the source signal has made it “difficult to find out which versions of CWP are or remain liable to this attack.”
For it is part, the dropper is sold with its own set of tasks, main among being detecting the particular runtime environment, decrypting some sort of configuration file to get C2 information, configuring the rootkit, and starting the rootkit by injecting it in to the secure shell server method (sshd).
Rootkits are particularly harmful as they allow attackers to get elevated privileges in the method, allowing them to interfere with core functions conducted by the underlying computer. This ability of rootkits to camouflage into the materials of the operating system gives assailants a high level of stealth plus evasion.
Facefish also uses a complex communication protocol plus encryption algorithm, using guidance starting with 0x2XX to exchange open public keys and BlowFish to get encrypting communication data while using C2 web server. Some of the C2 commands sent by the server are as follows –
- 0x300 – Report stolen credential information
- 0x301 – Collect details of “uname” command
- 0x302 – Run slow shell
- 0x310 – Execute almost any system command
- 0x311 – Deliver the result of bash execution
- 0x312 – Report host information
NETLAB’s conclusions come from an analysis of the ELF sample file the item detected in February 2021. Other indicators of skimp on associated with the malware can be utilized here.
[ad_2]
Source link