[ad_1]
Cybersecurity researchers have shared a new backdoor program efficient at stealing user login references, device information and doing arbitrary commands on Cpanel systems.
The malware dropper has been dubbed “Facefish” simply by Qihoo 360 NETLAB crew owing its capabilities to supply distinct rootkits at different times and the use of Blowfish cipher to encrypt marketing and sales communications to the attacker-controlled server.
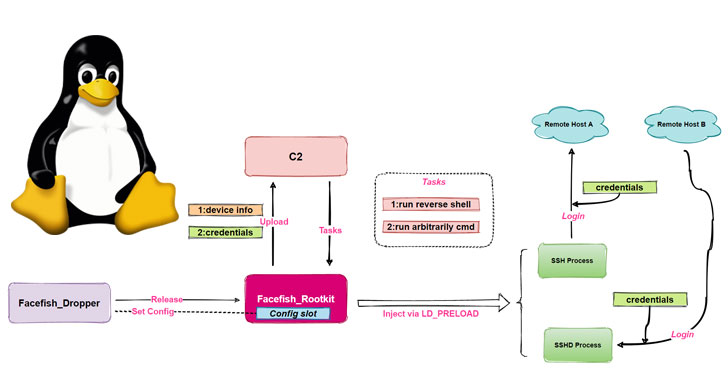
“Facefish consists of 2 parts, Dropper and Rootkit, and its major function is determined by the Rootkit module, which works in the Ring 3 layer and is packed using the LD_PRELOAD feature of stealing user login credentials simply by hooking ssh/sshd program associated functions, and it also supports many backdoor functions,” the particular researchers said.
The NETLAB research builds on a earlier analysis published by Wacholder Networks on April twenty six, which documented an attack company targeting Control Web -panel (CWP, formerly CentOS Website Panel) to inject a SSH implant with records exfiltration capabilities.
Facefish experiences a multi-stage infection approach, which commences with a control injection against the CWP to be able to retrieve a dropper (“sshins”) from a remote server, which in turn releases a rootkit which will ultimately takes charge connected with collecting and transmitting hypersensitive information back to the storage space, in addition to awaiting further guidelines issued by the command-and-control (C2) server.
For its aspect, the dropper comes with its set of tasks, chief amongst being detecting the runtime environment, decrypting a construction file to get C2 details, configuring the rootkit, and even starting the rootkit simply by injecting it into the safeguarded shell server process (sshd).
Rootkits are particularly dangerous when they allow attackers to gain enhanced privileges in the system, permitting them to interfere with core operations carried out by the underlying operating system. This particular ability of rootkits to be able to camouflage into the fabric on the operating system gives attackers if you are an00 of stealth and forestalling.
Facefish also employs a fancy communication protocol and security algorithm, using instructions guidance 0x2XX to exchange public take some time and BlowFish for encrypting communication data with the C2 server. Some of the C2 directions sent by the server are usually as follows –
- 0x300 – Record stolen credential information
- 0x301 – Collect details of “uname” command
- 0x302 – Run reverse shell
- 0x310 – Execute any method command
- 0x311 – Send a result of bash execution
- 0x312 – Record host information
NETLAB’s findings originate from an analysis of an ELF sample file it recognized in February 2021. Various other indicators of compromise for this malware can be accessed here.
[ad_2]
Source link